The World After Snowden
Growth of Encrypted Network Traffic
Technology advances to secure network traffic — global cybersecurity dialogue needed
What we are seeing confirms that now is the time for the world to come together on cybersecurity.
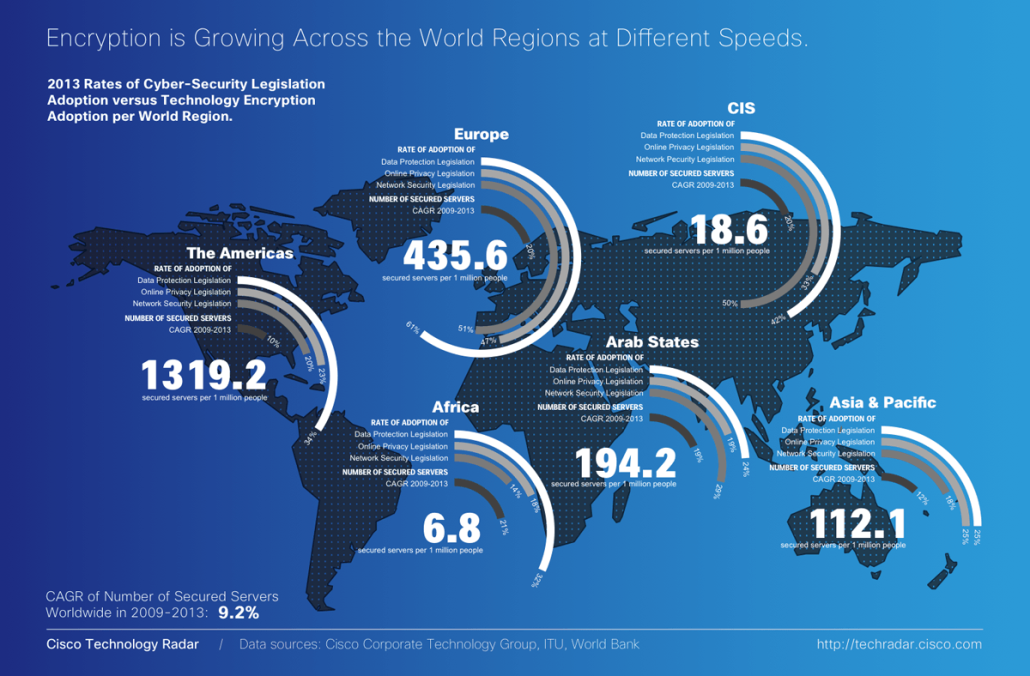
The technical community is actively creating solutions to secure network traffic. Patent filings show a compound annual growth rate (CAGR) of 12.3 percent from 2009 to 2013. The innovation boost, together with other factors, has led to an upsurge in encrypted network traffic. In the same period, the number of secured servers worldwide grew at a CAGR of 9.2 percent. This is a positive sign of advancement.
Encryption and information privacy are not converging into common practices, however. People, industries, and regions around the world confront the issue of cybersecurity in different ways.
Ultimately, this varied approach could raise barriers to the free flow of information online. And the economic consequences could be severe: by 2016, the Internet economy in G-20 nations is expected to account for 5.3 percent of Gross Domestic Product.
A global dialogue among all stakeholders, including governments, society, and the private sector, can help create agreement on how to secure the Internet economy. In the meantime, with the progress the IETF and other standards bodies are making, the future looks promising.
Next-generation encryption – NSA-proof SSH
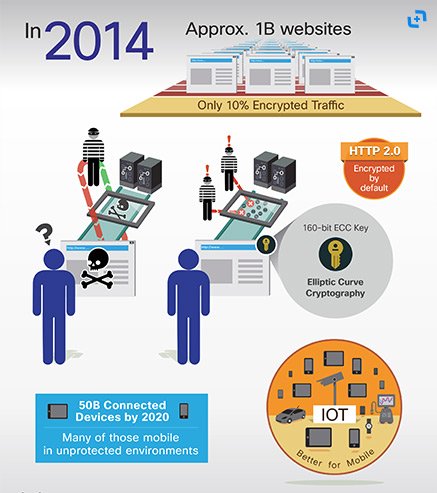
- Next-generation encryption efforts based on Elliptic Curve Cryptography (ECC) are promising. They provide the same level of encryption strength with shorter keys.
- The benefit is lower CPU consumption and low memory usage, two essential requirements for mobile devices such as sensors, actuators, controllers, and microcomputers, and the Internet of Things (IoT).
- As a result High Complex Encryption is becoming common and cheap
SSH version 1:
- Ciphers: “blowfish”, “3des”, and “des”
SSH version 2:
- Ciphers: aes256-gcm@openssh.com,aes128-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr
- MACs: hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512
- KexAlgorithms: curve25519-sha256@libssh.org,diffie-hellman-group-exchange-sha256
A tectonic shift for the Internet’s crypto landscape is coming
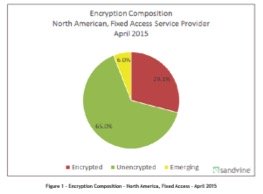
The current share of encrypted traffic on the web is largely due to Google, Facebook and Twitter, which have all by now adopted HTTPS by default.
- Netflix dominates the world’s digital pipes
- More than 40 million subscribers in the United States
- About 60 million globally
- 10 billion hours of video streamed in the first quarter of the year, Netflix accounts for more than a third of all downstream (or downloaded) north American Internet traffic during peak evening hours
- Netflix: “Over the next year we’ll evolve from using HTTP to using Secure HTTP (HTTPS) while browsing and viewing content on our service.
- This helps protect member privacy, particularly when the network is insecure, such as public WIFI, and it helps protect members from eavesdropping by their ISP or employer, who may want to record our members’ viewing for other reasons”
Let’s Encrypt is a new free Certificate Authority
Let’s Encrypt is a free, automated, and open certificate authority brought to you by the Internet Security Research Group (ISRG). ISRG is a California public benefit corporation, and is recognized by the IRS as a tax-exempt organization under Section 501(c)(3) of the Internal Revenue Code.
Let’s Encrypt is a new Certificate Authority:
It’s free, automated, and open.